To increased security to your AWS root account, Amazon web services recommend configuring multi-factor authentication (MFA) to help protect your AWS resources. MFA adds extra security because it requires users to type a unique authentication code from an approved authentication device or SMS (Short Message Service) text message when they access AWS websites or services.
Security token-based type of MFA requires you to assign an MFA device (hardware or virtual) to the IAM user or the AWS account root user. A virtual device is a software application running on a phone or other mobile device that emulates a physical device. Either way, the device generates a six-digit numeric code based upon a time-synchronized one-time password algorithm. The user must type a valid code from the device on a second webpage during sign-in. Each MFA device assigned to a user must be unique; a user cannot type a code from another user’s device to authenticate. For more information about enabling security token-based MFA, see Enabling a Hardware MFA Device (Console) and Enabling a Virtual Multi-factor Authentication (MFA) Device (Console).
When you enable MFA for the AWS account root user, it affects only the root user credentials. IAM users in the account are distinct identities with their own credentials, and each identity has its own MFA configuration.
To enable a virtual MFA device
- Sign in to the AWS Management Console and open the IAM console at https://console.aws.amazon.com/iam/.
- Under Security status, Activate MFA on your root account
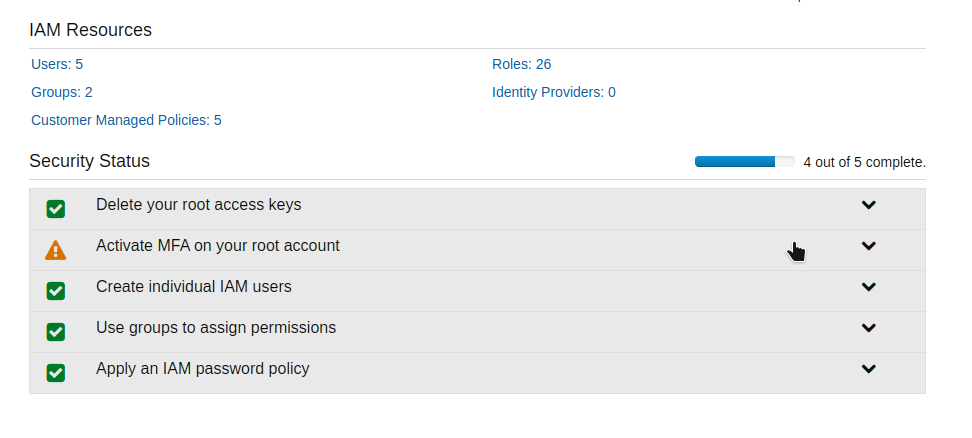
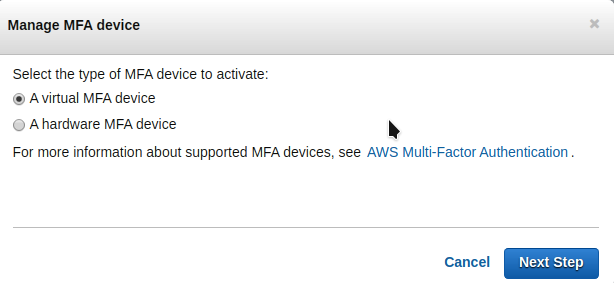
- In the Manage MFA Device wizard, choose A virtual MFA device, and then choose Next Step.
- IAM generates and displays configuration information for the virtual MFA device, including a QR code graphic. The graphic is a representation of the ‘secret configuration key’ that is available for manual entry on devices that do not support QR codes.
- Open your virtual MFA app. ( You can also use Google Authenticator ),
- Use the app to scan the QR code. For example, you might choose the camera icon or choose an option similar to the Scan code, and then use the device’s camera to scan the code.
- The virtual MFA device starts generating one-time passwords.
- In the Manage MFA Device wizard, in the Authentication Code 1 box, type the one-time password that currently appears in the virtual MFA device. Wait up to 30 seconds for the device to generate a new one-time password. Then type the second one-time password into the Authentication Code 2 box.
- Choose Active Virtual MFA.
After Activating MFA, while you log in you have to enter the OTP generated in your MFA virtual device along with username and password