What is Vulnerability Scanning
Vulnerability scanning is the process of inspecting the security weaknesses that exist in the software. With a good vulnerability scanner, you can bring to light the security, licensing, and code quality issues that may affect the well-being of software.
Vulnerability scanning, also commonly known as ‘vuln scan,’ is a process of proactively identifying network, application, and security vulnerabilities. Vulnerability scanning is typically performed by the IT department of an organization or a third-party security service provider. This scan is also performed by attackers who try to find points of entry into your network.
“A weakness in the computational logic (e.g., code) found in software and hardware components that, when exploited, results in a negative impact to confidentiality, integrity, or availability. Mitigation of the vulnerabilities in this context typically involves coding changes, but could also include specification changes or even specification deprecations (e.g., removal of affected protocols or functionality in their entirety).”
CVE definition of vulnerability
How does vulnerability scanning work?
Depending on the type of scan the vulnerability platform uses, various techniques and tactics will be leveraged to elicit a response from devices within the target scope. Based on the devices’ reactions, the scanner will attempt to match the results to a database and assign risk ratings (severity levels) based on those reactions.
Vulnerability scanners can be configured to scan all network ports, detecting and identifying password breaches as well as suspicious applications and services. The scanning service reports security fixes or missing service packs, identifies malware as well as any coding flaws and monitors remote access.
A vulnerability scanner works by providing visibility into your software and suggesting fixes to mitigate the risks related to open source usage. It does this by running through a list of checks to establish if your codebase has vulnerabilities reported in the public databases and security advisories. These resources, such as the popular National Vulnerability Database, reference known security-related software defects, coding bugs, misconfigurations, and other flaws that attackers can exploit.
What is the need for Open-Source Vulnerability scanning
Today Open Source is everywhere, Open source is no more the work of hobbyists and lone developers. Today much of the work on the open-source software is backed by corporate companies, Say Adobe is having a strong commitment to open-source and has around 650 repositories in GitHub and their developers are actively contributing to other repositories, there are a lot of opensource tools and libraries we are using today. Many organizations and individuals are benefitted from using open-source libraries to accelerate their development cycle.
Along with a lot of benefits, open-source software comes with several risks because of code quality and the security vulnerabilities in the code so the organization needs to run the vulnerability scanning regularly for the open-source libraries they are using.
The main way to identify vulnerabilities is through vulnerability scanning, and a scanner’s efficacy depends on two things:
- The ability of the scanner to locate and identify devices, software, and open ports, and gather other system information
- the ability to correlate this information with known vulnerability information from one or more vulnerability databases
How WhiteSource Bolt Can Assist
WhiteSource Bolt is a free vulnerability scanning tool that can help you overcome the security risks of using open-source software. It’s available as a free app on GitHub or as a free extension on Azure DevOps Services. With Bolt, you can automatically scan your projects and match the open-source components against the known vulnerabilities, security risks, code fixes, and updates. It assists you to ensure you’re using high-quality open source components as well as licenses that fit your desired business model.
WhiteSource Bolt for GitHub
WhiteSource Bolt for GitHub is a FREE app, which continuously scans all your repos, detects vulnerabilities in open source components, and provides fixes. It supports both private and public repositories.
Major Supported Languages : C, C#, C++, Go, Java, JavaScript, Objective-C, PHP, Python, and Ruby
WhiteSource Bolt for GitHub scans your repos every time you apply a push (limited to 5 scans/day per repo) and opens an issue for every vulnerable open source library. The issue will include reference links, a dependency tree (if exists), vulnerability info, and suggested fixes. Using GitHub Checks, a report will be created with all new vulnerabilities, enabling you to prevent merging pull requests.
To install in your GitHub account
Open the marketplace > apps > WhiteSource Bolt or open the link https://github.com/marketplace/whitesource-bolt
At the end of the page you have option to choose WhiteSource Bolt and install it for free
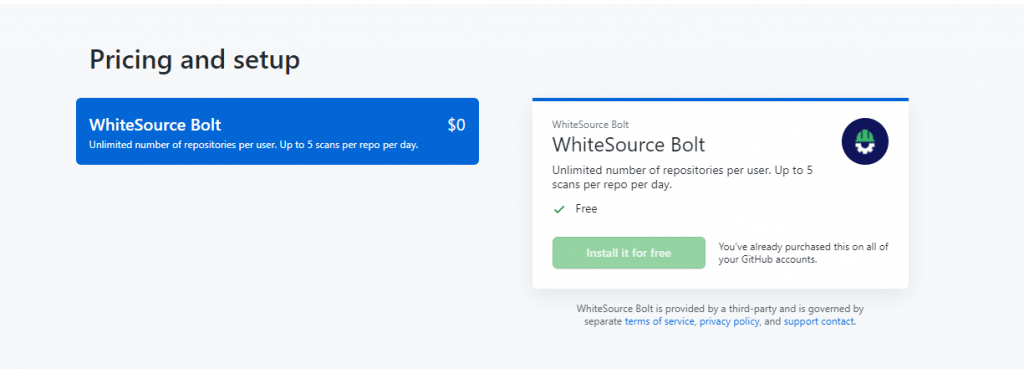
After completing the setup, you need to provide your repository access to WhiteSouce Bolt
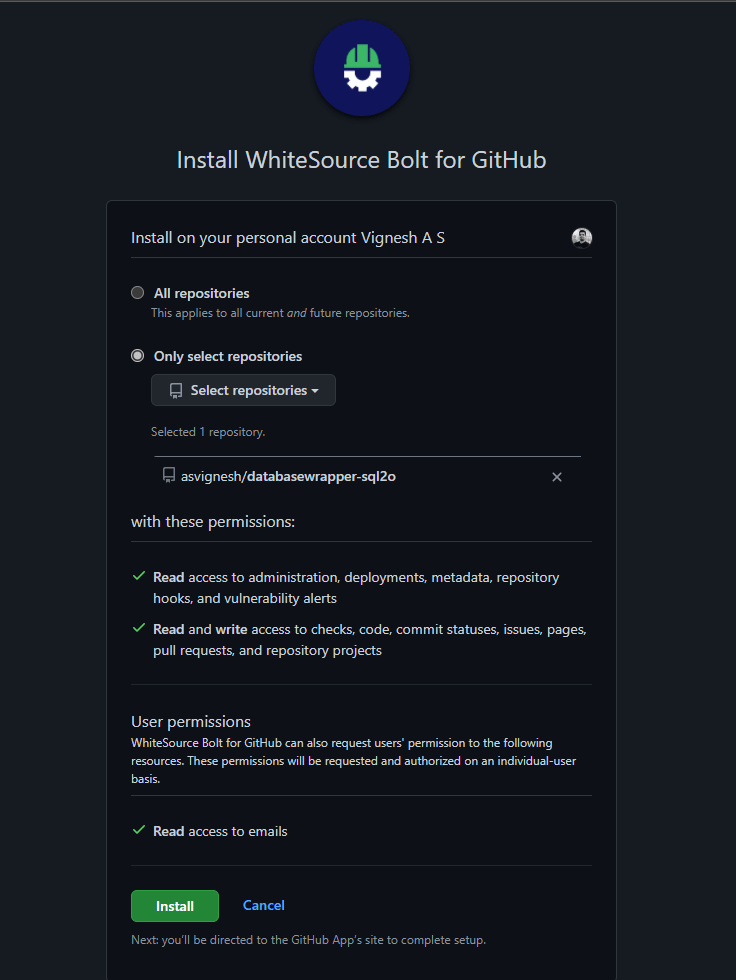
You can either install for all repo or choose the repository you want to scan, then Click Install to install it.
The installation will redirect you to the Registration Page where you need to accept the terms and privacy policy to proceed
Once the Installation completed, you can see a pull request to your repository from whitesource/configure
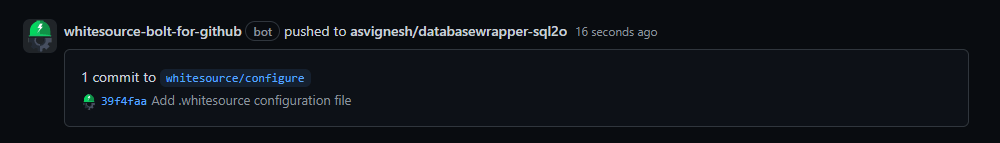
This PR contains a ‘.whitesource’ configuration file that can be customized to your needs. If no changes were applied to this file, WhiteSource Bolt for GitHub will use the default configuration.
Before you merge the Pull request, make sure you enabled the Issues feature for your repository
Once you merge this PR, WhiteSource Bolt for GitHub will scan your repository and create a GitHub Issue for every vulnerability detected in your repository.
If you do not want a GitHub Issue to be created for each detected vulnerability, you can edit the ‘.whitesource’ file and set the ‘minSeverityLevel’ parameter to ‘NONE’.
{
"scanSettings": {
"baseBranches": []
},
"checkRunSettings": {
"vulnerableCheckRunConclusionLevel": "failure",
"displayMode": "diff"
},
"issueSettings": {
"minSeverityLevel": "NONE"
}
} How to trigger a new Scan
Each repository can be scanned up to 5 times a day, Scan can be initialized by adding a valid push command to the repository
The valid command means
- One of the commits in the ‘push’ command includes added file(s) that have an extension supported by WhiteSource and/or one of the commits in the ‘push’ command included removal of the file(s) that have an extension supported by WhiteSource. Refer to the WhiteSource Languages page in order to find out whether or not a specific language and its extensions are supported.
- One of the commits in the ‘push’ command includes a modification in the package manager configuration file(s). This includes any of the following files, as specified here.
Issues
The Issues tab displays all the issues which the WhiteSource Bolt identified, the application creates a proprietary label in the Issues named “security fix” and “security vulnerability”
In the issue the Common Vulnerability Scoring System 3 Score and the suggestion to fix the issue will be mentioned
- CVSS 3 score: Basic CVSS3 score matrix. If this score is not available then the CVSS 2 score matrix is displayed.
- The suggested fix for the vulnerability: A detailed suggestion that includes type, origin, release date, and fix resolution. Note that a fix may not always be available.
Also published on Medium.



